The NIST Cybersecurity Framework provides a basic and understandable language of five key Functions– Identify, Protect, Detect, Respond, and Recover – for managing risk iteratively over time.
Our team is trained to walk you through this framework and help you determine where you are at risk.
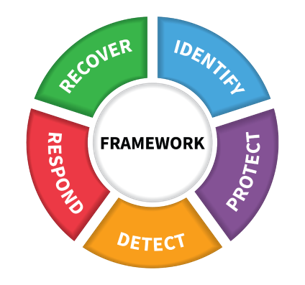
- Identify - Develop organizational understanding to manage cybersecurity risk to systems, assets, data, and capabilities.
- Protect - Develop and implement the appropriate safeguards to ensure delivery of services.
- Detect - Develop and implement the appropriate activities to identify the occurrence of a cybersecurity event.
- Respond - Develop and implement the appropriate activities to take action regarding a detected cybersecurity event. Recover - Develop and implement the appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity event.
Contact us to begin an audit of your cybersecurity infrastructure.




